Comprehensive Cloud Services: Increase Effectiveness and Safety And Security for Your Company
Comprehensive Cloud Services: Increase Effectiveness and Safety And Security for Your Company
Blog Article
Secure and Effective Information Management Through Cloud Solutions
In the ever-evolving landscape of information administration, the application of cloud services has emerged as a crucial option for organizations looking for to strengthen their data protection steps while improving operational effectiveness. universal cloud Service. The complex interaction between protecting sensitive info and making sure seamless availability positions a facility challenge that organizations need to navigate with diligence. By discovering the nuances of safe data management through cloud solutions, a much deeper understanding of the innovations and methods underpinning this standard shift can be unveiled, clarifying the multifaceted benefits and factors to consider that form the modern information monitoring community
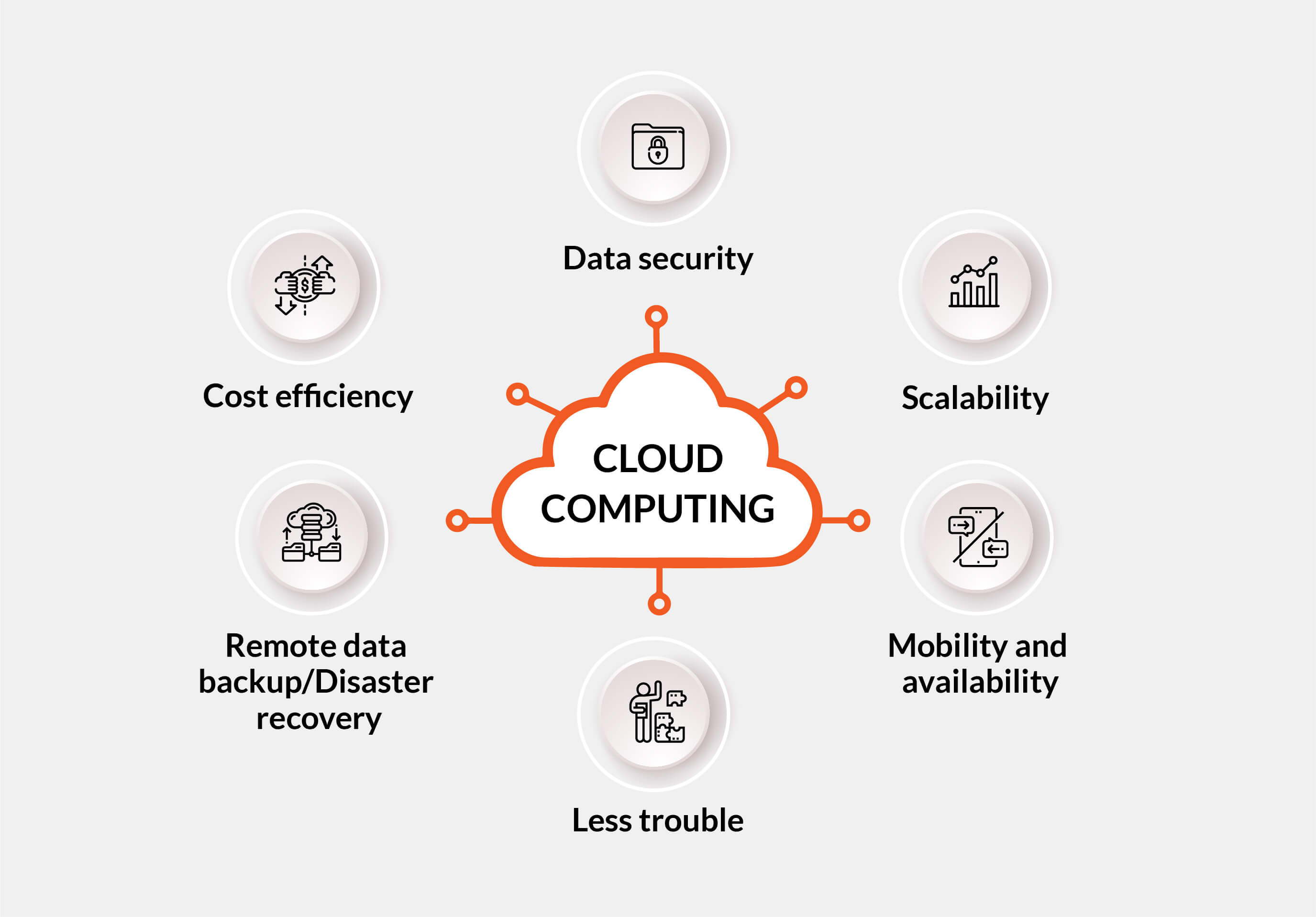
Value of Cloud Solutions for Data Administration
Cloud solutions play a critical function in contemporary data management methods because of their scalability, availability, and cost-effectiveness. Organizations can easily scale up or down their information storage space requires without the trouble of physical facilities expansion. This scalability permits services to adjust swiftly to changing information needs, making certain reliable procedures. In addition, cloud solutions give high access, enabling users to gain access to information from anywhere with a net connection. This availability promotes cooperation among groups, also those functioning from another location, bring about enhanced productivity and decision-making processes.
Furthermore, cloud services provide cost-effectiveness by getting rid of the need for purchasing pricey hardware and upkeep. Organizations can go with subscription-based designs that line up with their budget plan and pay just for the sources they use. This aids in decreasing upfront costs and general functional costs, making cloud solutions a viable option for companies of all dimensions. In significance, the relevance of cloud services in data monitoring can not be overstated, as they provide the necessary devices to enhance operations, improve partnership, and drive service development.
Secret Safety And Security Obstacles in Cloud Data Storage Space
To attend to these security difficulties, companies need durable protection steps, consisting of security, gain access to controls, routine security audits, and team training. Partnering with relied on cloud provider that provide sophisticated security features and compliance accreditations can additionally aid from this source mitigate threats related to cloud data storage. Eventually, a extensive and positive strategy to safety is vital in safeguarding data stored in the cloud.
Implementing Information File Encryption in Cloud Solutions
Carrying out data file encryption in cloud services entails utilizing robust encryption algorithms and safe essential monitoring practices. Security secrets ought to be saved independently from the encrypted data to include an extra layer of security. Additionally, companies need to on a regular basis update security tricks and use strong gain access to controls to limit that can decrypt the data.
Additionally, data encryption ought to be applied not only throughout storage space however also throughout data transmission to and from the cloud. Safe and secure communication methods like SSL/TLS can aid protect information in transportation, guaranteeing end-to-end file encryption. click resources By prioritizing data encryption in cloud services, companies can bolster their information security posture and keep the discretion and honesty of their sensitive details.
Ideal Practices for Information Backup and Recovery

Moreover, carrying out regular recuperation drills is crucial to test the effectiveness of backup treatments and the company's ability to bring back data promptly. File encryption of backed-up data adds an added layer of safety and security, guarding sensitive information from unauthorized accessibility throughout storage space and transmission.
Surveillance and Auditing Information Access in Cloud
To preserve data honesty and protection within cloud environments, it is crucial for organizations to develop durable procedures for surveillance and bookkeeping information gain access to. Auditing information access goes a step even more by providing a detailed record of all data accessibility tasks. Cloud solution suppliers commonly use devices and solutions that promote surveillance and bookkeeping of data accessibility, allowing companies to gain understandings into just how their data is being used and ensuring responsibility.
Conclusion
To conclude, cloud services play a crucial function in making certain protected and effective data administration for organizations. By addressing crucial security obstacles through data file encryption, back-up, recuperation, and checking practices, companies can safeguard sensitive information from unapproved accessibility and data breaches. Carrying out these ideal techniques in cloud services promotes information stability, discretion, and ease of access, eventually improving partnership and productivity within Visit Your URL the company.
The vital safety and security difficulties in cloud data storage space revolve around information violations, information loss, conformity regulations, and information residency concerns. By securing data prior to it is published to the cloud, companies can minimize the risk of unauthorized gain access to and data breaches. By prioritizing information security in cloud remedies, companies can strengthen their information safety posture and maintain the discretion and stability of their delicate info.
To maintain data honesty and safety within cloud settings, it is necessary for companies to establish robust measures for surveillance and bookkeeping data accessibility. Cloud solution suppliers usually use tools and services that promote tracking and auditing of information gain access to, enabling companies to get insights right into just how their information is being utilized and ensuring liability.
Report this page